Operation
The entropy byte-stream provided in the AlphaRNG output is based on electrical noise produced by two Zener diodes working in avalanche mode. The independent electrical noise created by each electrical circuit is amplified and sampled into independent, raw byte-streams and has a uniform distribution of the random values. The two resulting raw byte-streams are then combined and de-biased to produce the resulting entropy byte stream. The AlphaRNG software kit provides an API for retrieving data at each processing stage for the purpose of evaluation or, for example, when a different post-processing or conditioning algorithm is to be used.
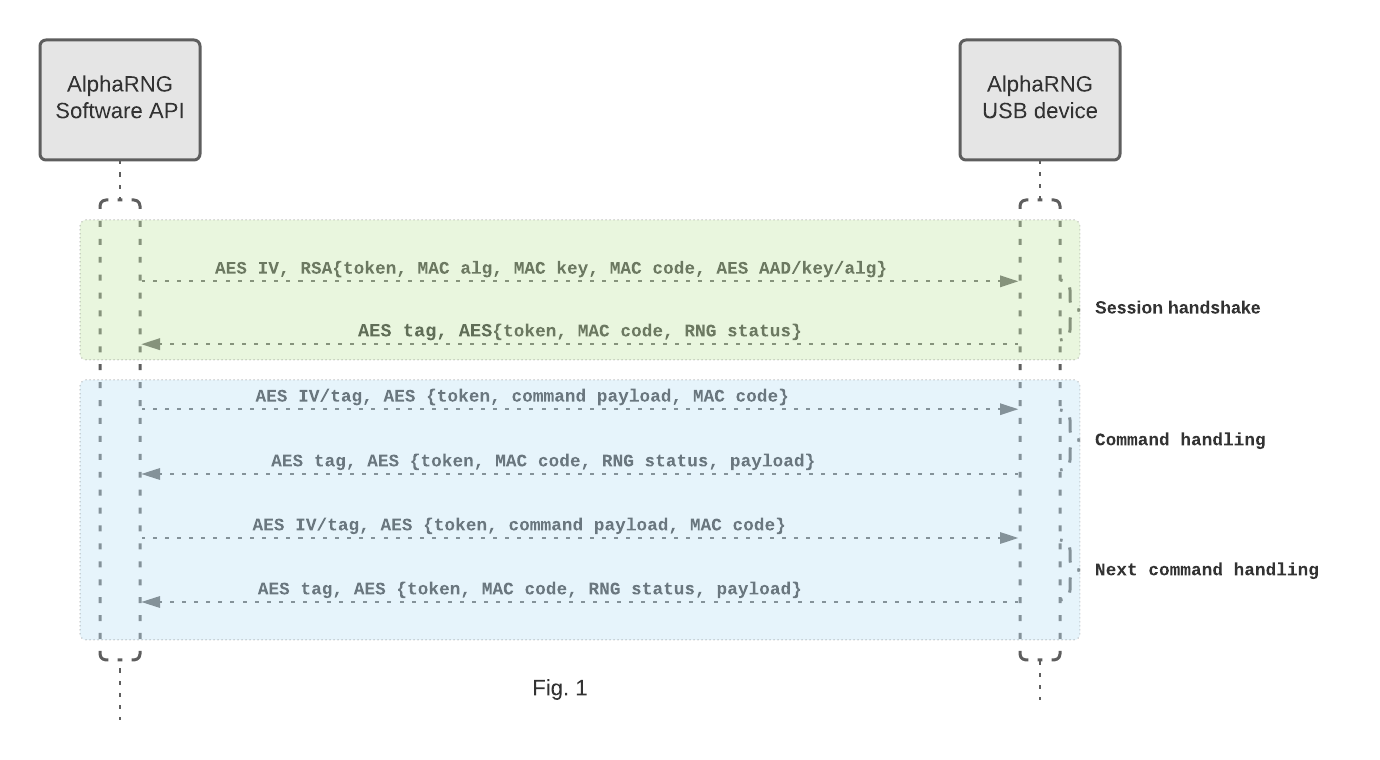
The AlphaRNG implements an API for establishing a secure connection with a computer over a USB interface. The secure connection is initiated on the computer by using the AlphaRNG software API (client). Once the client establishes a successful connection over the USB interface, the client creates a session request, encrypts it with the public RSA key, and sends it to the AlphaRNG (see Fig. 1). A session request consists of parameters such as symmetric cipher, randomly created cipher key, a new non reusable cipher IV, cipher AAD, MAC algorithm, randomly created MAC key, a new unique non-reusable request token, and a new generated MAC value of the plain request. The AlphaRNG receives the session request, decrypts it with its secret RSA key, generates its own MAC value of the plain request (using the MAC key provided in same request), and compares it with the MAC value provided in the request. Upon successful validation of the session request, the AlphaRNG will store new session parameters and use those for the duration of the session. It then creates a response packet, encrypts it with the session cipher and key/IV/AAD provided, and sends the response packet back to the client. A response packet consists of session cipher used, cipher tag, request token, MAC value of the plain response, and RNG internal status code. The client receives the response, decrypts it with the session cipher using key/IV/AAD and cipher tag provided, generates its own MAC value of the plain response and matches it against the one provided, then it compares the provided token in the response with the one initially generated for the session request. Once the response is validated, the session is successfully established, and the client can securely communicate with the AlphaRNG device over the USB interface.
Once a secure connection has been established, the client can send commands to the AlphaRNG and receive responses. The client creates a command packet, generates the MAC value (using the session MAC algorithm and the MAC key) of the plain command data, and includes it in the packet. It then encrypts the packet with the session cipher and the key/IV/AAD and sends it to the USB device. The command packet consists of parameters such as the cipher used, a new non-reusable cipher IV, cipher tag, MAC value of the plain command data, command ID, and a freshly generated unique non-reusable command token. The AlphaRNG receives the command and decrypts it with session cipher and the key/AAD/IV, generates the MAC value using the session MAC algorithm and the MAC key, and compares the MAC value with the one provided in command packet. Upon successful command validation, the AlphaRNG handles the command, creates a response packet, generates the MAC value, encrypts the response packet with the session cipher and the key/IV/AAD and sends the response packet back to the client. A response packet consists of the session cipher used, the command token, the cipher tag, the MAC value of the plain response, the data payload, and the RNG internal status code. The client receives the response, decrypts it with the session cipher using key/IV/AAD and cipher tag provided, generates its own MAC value of the plain response, and compares it against the one provided in the packet - then it compares the provided token in the response with the one initially generated for the command packet. Upon successful validation of the response packet, the client validates the RNG internal status and dispatches the response payload accordingly.
The AlphaRNG software kit includes two pre-installed public keys: a 2048-bit RSA key and a 1024-bit RSA key. These keys allow you to securely connect to any AlphaRNG device. Moreover, each AlphaRNG comes with its own unique 2048-bit RSA public key, providing an additional layer of security for exclusive use with that specific device.
Supported systems
- Linux (x86, x64, ARM)
- or FreeBSD 12/13/14
- or macOS (Intel and M1 chips)
- or 64 bit Windows 10/11, 64 bit Windows Server 2016/2019
Fabrication and testing
All AlphaRNG devices are designed, assembled, programmed, and tested in the United States. After each device is assembled, both random noise sources are individually inspected and verified. The device does not require any tune-up after it is assembled, and the quality of the entropy produced remains constant.
Operating temperature
- Maximum ambient temperature when in active mode: 81°F (27°C). The connected device should be located at least 1 inch away from other USB devices in an area with a free or forced air flow circulation.
Other information
- Weight: 22 grams (0.8 oz)
- Lead-free and RoHS compliance: All parts and materials used in AlphaRNG devices are lead free and RoHS compliant.
- The AlphaRNG draws no more than 220 mA.
- Filled inside with an epoxy compound for protection and heat dissipation.