Intro
AlphaRNG is a hardware random number generator that can produce high quality true random numbers. AlphaRNG implements data communications over a secure channel using a USB interface. More documentation is available at this location.
Hardware requirements
Compatible with USB 2.0 high-speed and USB 1.1 full-speed interface specifications, the AlphaRNG device can be plugged into one of the available USB 2.0, USB 1.1 or USB 3.0/3.1 ports.
OS requirements
- Linux (x86, x64, ARM)
- or FreeBSD 12/13/14
- or macOS (Intel and M1 chips)
- or 64 bit Windows 10/11, or 64 bit Windows Server 2016/2019
Windows
Device driver installation for 64 bit Windows 10/11
Once an AlphaRNG device is plugged into one of the USB ports available, an appropriate driver will be installed by the OS.
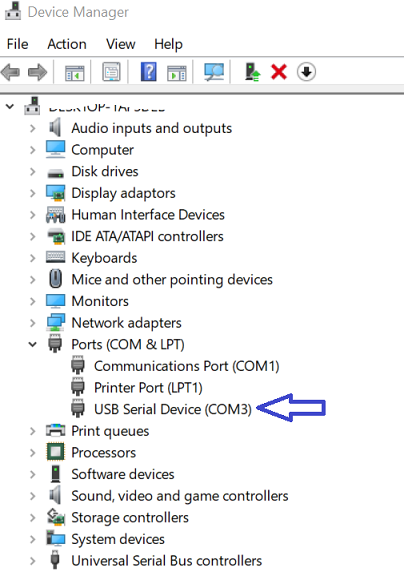
When the Windows driver is successfully installed for the AlphaRNG device, a USB Serial Device entry should show up under the Ports (COM & LPT) group in the Device Manager application as shown in the following screenshot:
Using pre-built Windows utilities and components
AlphaRNG software kit contains pre-built utilities and components that can be used on Windows. You can download the latest alrng-windows-binaries.zip here.
The pre-built utilities require OpenSSL-Win64 version 1.1.1j or newer. To install it on Windows x64 platform visit the following
URL, the download links are provided in Download Win32/Win64 OpenSSL section.
alrng-windows-binaries.zip contains folder windows-x64-vs-2019 with binary executables and dependencies for 64-bit Windows, built with Visual Studio 2019.
To verify if the AlphaRNG device has been installed successfully, locate ‘alrng.exe’ utility which is available in the folder mentioned above, and run it on command line prompt as following:
alrng.exe -l
If the device is successfully installed and ready for usage, the output may look like this:
Device 0: 'Alpha True RNG ', S/N: F0383F99E34084B, version: 1.0
You can also use alrngdiag.exe to run the AlphaRNG device diagnostics. It should not report any failures or warnings during execution.
Linux
Downloading the software kit
AlphaRNG software kit doesn’t include binaries for Linux platforms. You will need to download the source code and build utilities and components for specific OS. The AlphaRNG software kit can be downloaded from this location. Alternatively it can be downloaded with git using the following command:
git clone https://github.com/tectrolabs/alpharng.git
Locate the source code with the following command:
cd alpharng/linux-and-macOS/alrng/
Prerequisites
Make sure make, openssl 1.1+, libssl and c++ 11 components are installed before running the build.
Ubuntu
On Ubuntu, use the following commands to install the required dependencies:
sudo apt install make
sudo apt install g++
sudo apt install openssl
sudo apt install libssl-dev
CentOS and Red Hat
On CentOS or Red Hat, use the following commands to install the required dependencies:
sudo yum install make
sudo yum install gcc-c++
sudo yum install openssl
sudo yum install openssl-devel
Building utilities and components
To build and install utilities you will need to run the following from the command line:
make
sudo make install
The build may fail when using older versions of OpenSSL. You can check the current version installed with openssl version command. Make sure that you have installed an OpenSSL version 1.1.0 or newer.
To verify if the AlphaRNG device has been installed successfully, run the following on command line prompt:
sudo alrng -l
If the device is successfully installed and ready for usage, the output may look like this:
Device 0: 'Alpha True RNG ', S/N: F0383F99E34084B, version: 1.0
In addition you can also use alrngdiag to run the AlphaRNG device diagnostics. It should not report any failures or warnings during execution.
Using ‘alrng’ utility for retrieving random data
To retrieve 12,000 entropy bytes (true random numbers) from the AlphaRNG device to a file over a secure connection:
sudo alrng -e -o rnd.bin -n 12000
Linux kernel module ‘alrandom’
Please navigate to this location for the details about using alrandom kernel module.
Non-root access on Linux
To enable a non-root user to access the AlphaRNG device without specifying sudo, simply copy the supplied 85-alpharng-usb-access.rules file to /etc/udev/rules.d/ location with the following command:
sudo cp 85-alpharng-usb-access.rules /etc/udev/rules.d/
You may need to reboot the system for the changes to take effect.
macOS
Downloading the software kit
The AlphaRNG software kit doesn’t include binaries for MacOS platform. You will need to download the source code and build utilities and components for your Mac. The software kit can be downloaded here. Alternatively it can be downloaded with git using the following command:
git clone https://github.com/tectrolabs/alpharng.git
Locate the source code with the following command:
cd alpharng/linux-and-macOS/alrng/
Prerequisites
On macOS, the openssl 1.1+ dependency can be installed by running the following from the command line (make sure that Homebrew has been installed):
brew install openssl
Building utilities and components
To build and install utilities you will need to run the following from the command line:
make
sudo make install
To verify that the AlphaRNG device has been installed successfully, run the following on command line prompt:
alrng -l
If the device is successfully installed and ready for usage, the output may look like this:
Device 0: 'Alpha True RNG ', S/N: F0383F99E34084B, version: 1.0
In addition you can also use alrngdiag to run the AlphaRNG device diagnostics. It should not report any failures or warnings during execution.
Using alrng utility for retrieving random data using Windows
To retrieve 12,000 bytes of entropy directly from the AlphaRNG device to a file over a secure connection:
alrng -e -o rnd.bin -n 12000
Alternatively, you can use SHA-256 and SHA-512 entropy extractors, provided by the AlphaRNG Software Kit, for generating entropy bytes by applying SHA-256 (or SHA-512) method to concatenated RAW random bytes produced by both random noise sources. These methods comply with NIST SP 800 90B section 3.1.5.1 (Recommendation for the Entropy Sources Used for Random Bit Generation) and NIST FIPS PUB 180-4 (Secure Hash Standard). The extracted in/out ratio is 2/1 so that for every bit produced for output there will be 2 bits used for inout.
To retrieve 12,000 bytes of entropy using SHA-256 entropy extractor to a file over a secure connection:
alrng -x -o rnd.bin -n 12000
To retrieve 12,000 bytes of entropy using SHA-512 entropy extractor to a file over a secure connection:
alrng -X -o rnd.bin -n 12000
FreeBSD
Downloading the software kit
The software kit for FreeBSD can be downloaded here. Alternatively it can be downloaded with git using the following command:
git clone https://github.com/tectrolabs/alpharng.git
Locate the source code with the following command:
cd alpharng/linux-and-macOS/alrng/
Prerequisites
On FreeBSD, the gcc dependency can be installed by running the following from the command line:
sudo pkg install lang/gcc
Building utilities and components
To build and install utilities you will need to run the following from the command line:
make -f Makefile.bsd
sudo make -f Makefile.bsd install
To verify that the AlphaRNG device has been installed successfully, run the following on command line prompt:
sudo alrng -l
If the device is successfully installed and ready for usage, the output may look like this:
Device 0: 'Alpha True RNG ', S/N: F0383F99E34084B, version: 1.0
Using alrng utility for retrieving random data
To retrieve 12,000 bytes of entropy directly from the AlphaRNG device to a file over a secure connection:
sudo alrng -e -o rnd.bin -n 12000
Alternatively, you can use SHA-256 and SHA-512 entropy extractors, provided by the AlphaRNG Software Kit, for generating entropy bytes by applying SHA-256 (or SHA-512) method to concatenated RAW random bytes produced by both random noise sources. These methods comply with NIST SP 800 90B section 3.1.5.1 (Recommendation for the Entropy Sources Used for Random Bit Generation) and NIST FIPS PUB 180-4 (Secure Hash Standard). The extracted in/out ratio is 2/1 so that for every bit produced for output there will be 2 bits used for inout.
To retrieve 12,000 bytes of entropy using SHA-256 entropy extractor to a file over a secure connection:
sudo alrng -x -o rnd.bin -n 12000
To retrieve 12,000 bytes of entropy using SHA-512 entropy extractor to a file over a secure connection:
sudo alrng -X -o rnd.bin -n 12000
Using the supplied unique public RSA 2048-bit key
The AlphaRNG software kit comes with two hard-coded public keys: one RSA 2048 bit key and one RSA 1024-bit key. Those two keys are used for establishing secure connections with any AlphaRNG device. In addition, each AlphaRNG is shipped with a unique public RSA 2048-bit key that can be exclusively used with one such device.
To retrieve 12,000 random bytes from the AlphaRNG device to a file over a secure connection using the supplied unique public RSA 2048-bit key (you will need to run it with sudo permissions when used on Linux or FreeBSD platforms):
alrng -e -o rnd.bin -n 12000 -k public_key-XYZ.pem
Using AlphaRNG devices in virtual environment
AlphaRNG devices work with Linux, macOS, FreeBSD and Windows, and run in virtual machines using software such as VMware Player, VMware ESXi, VirtualBox, and Parallels. We have noticed however a decrease in projected AlphaRNG performance when using virtual machines. For best results, when used with virtual machines, we recommend connecting the AlphaRNG device to a USB port version 3 (or higher) or configuring the USB port as a pass-through device.